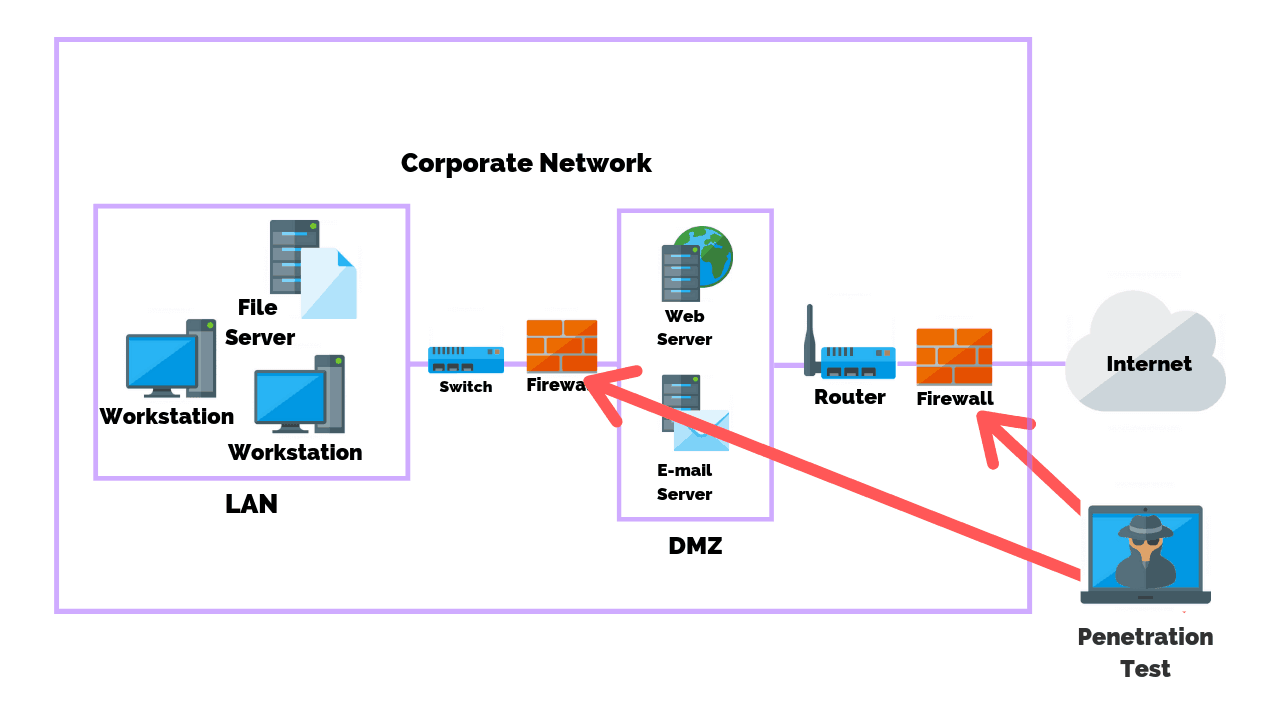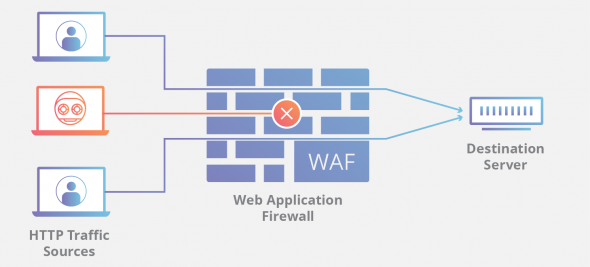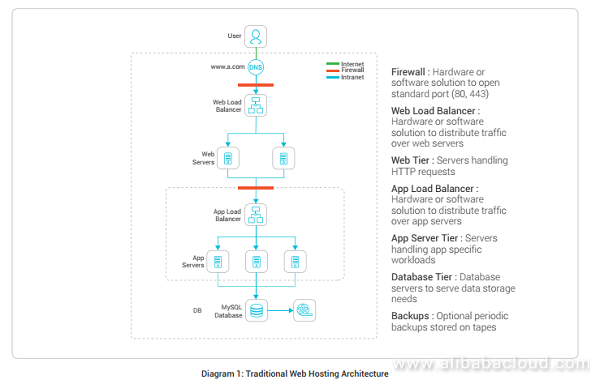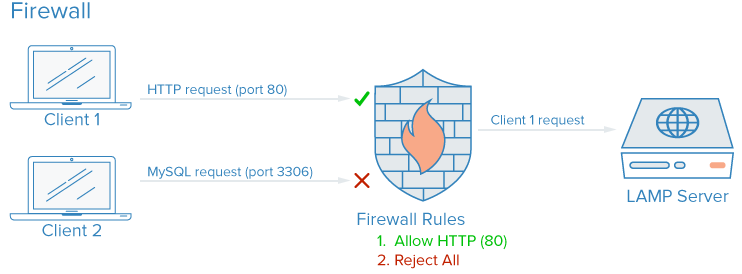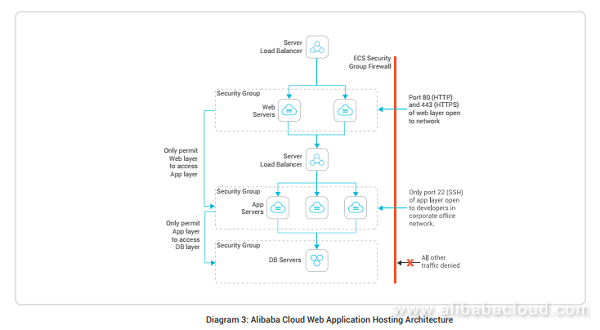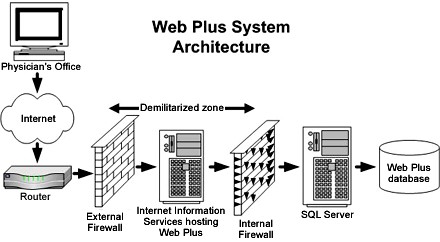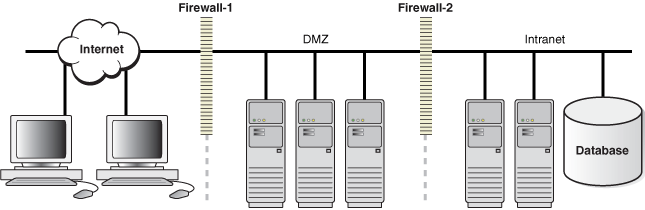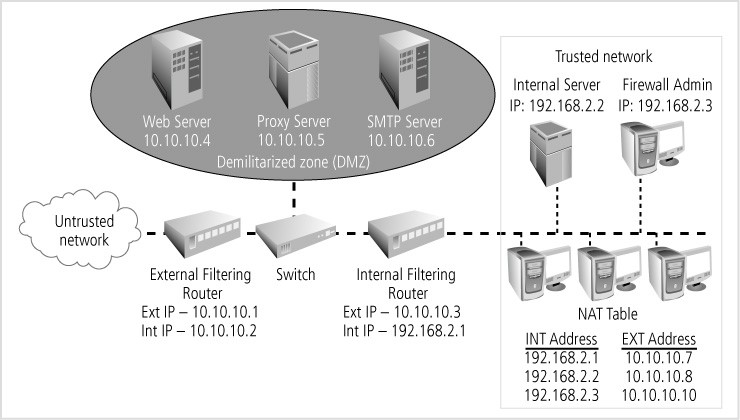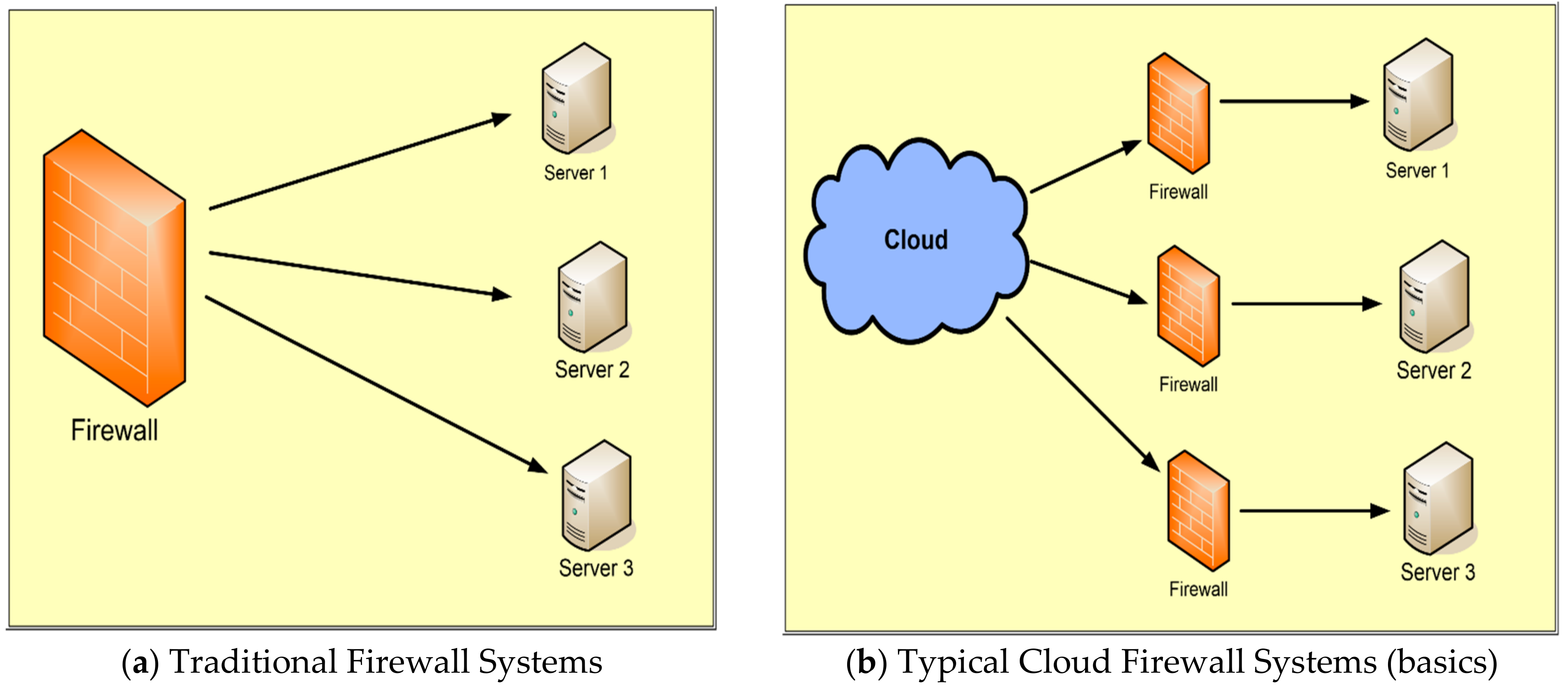
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review | HTML
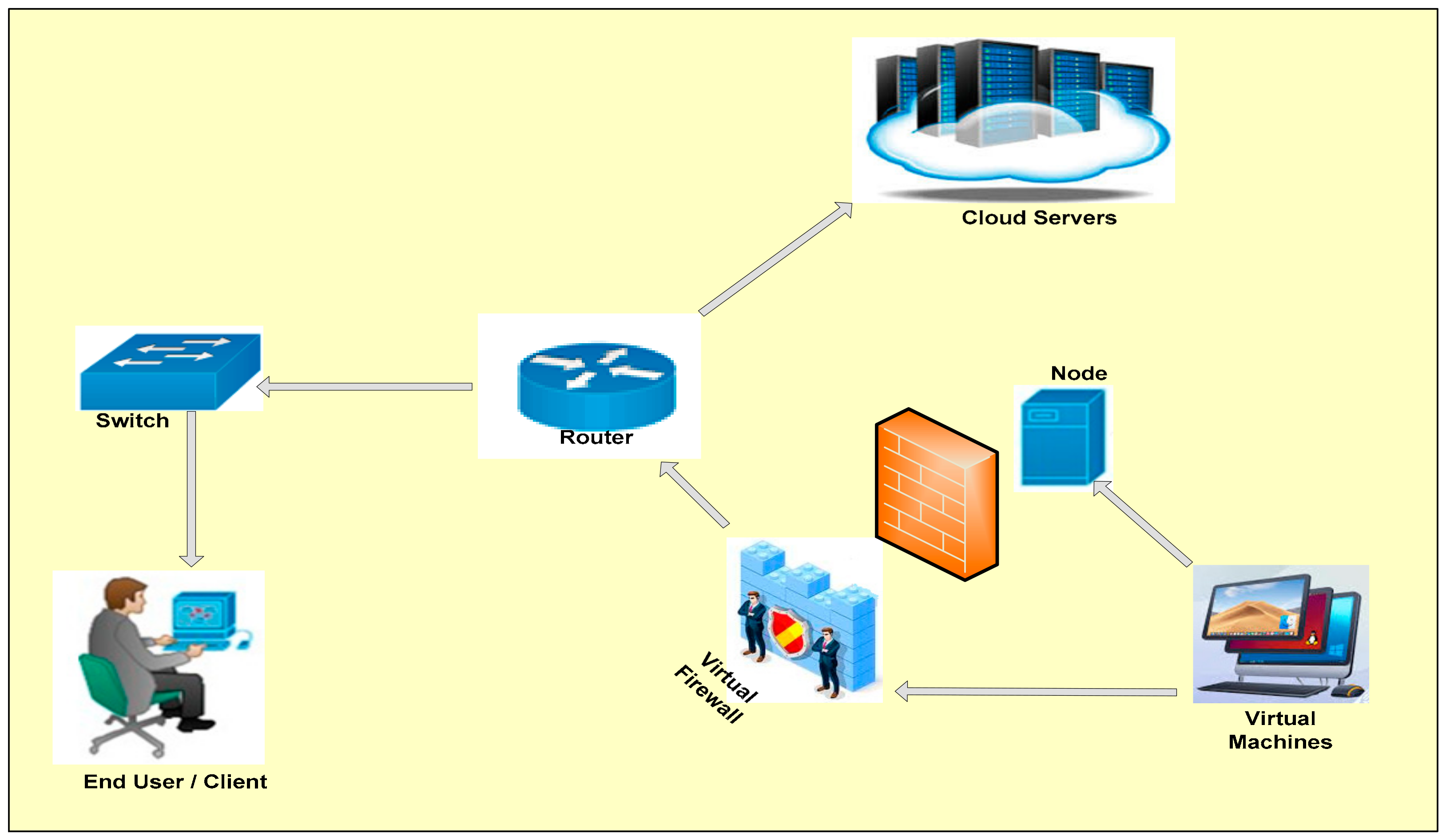
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review | HTML
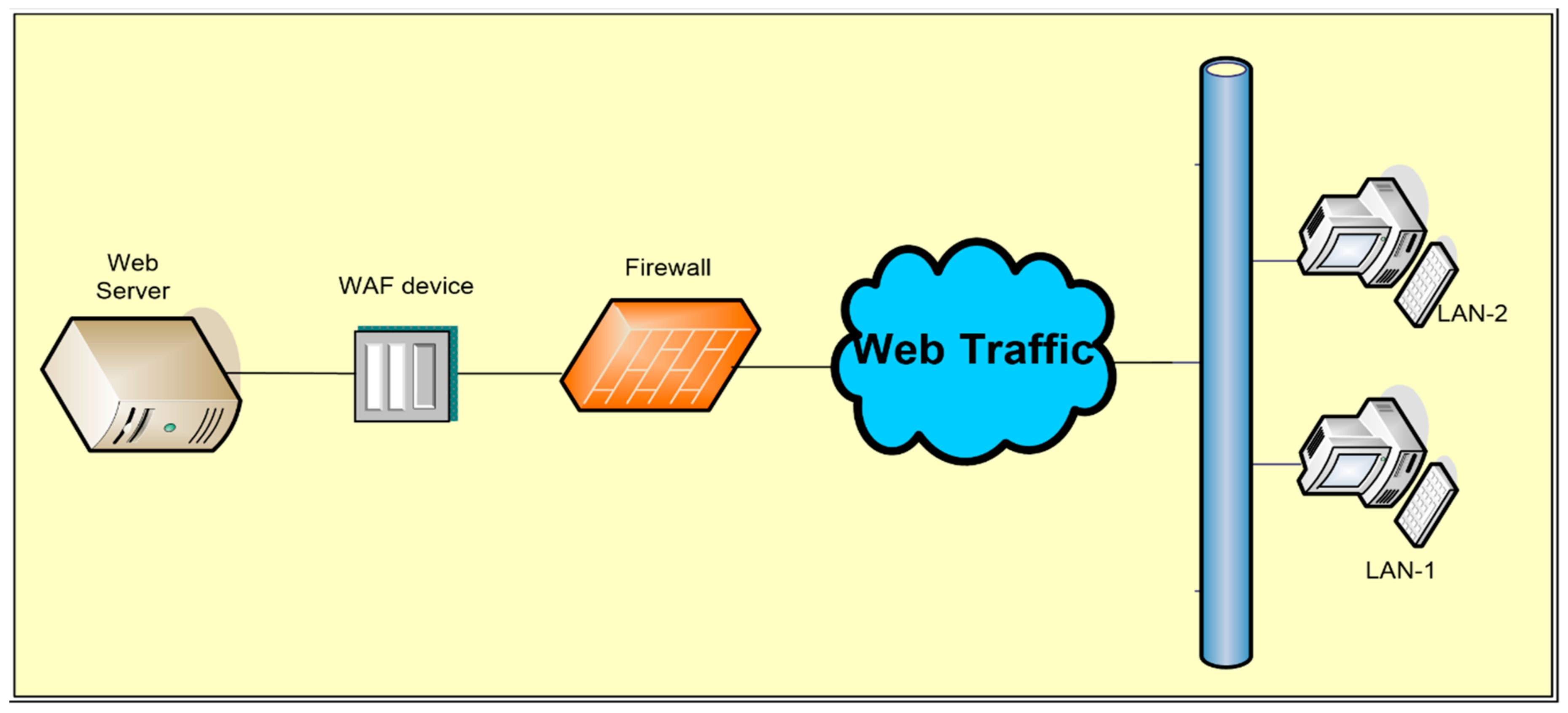
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review | HTML
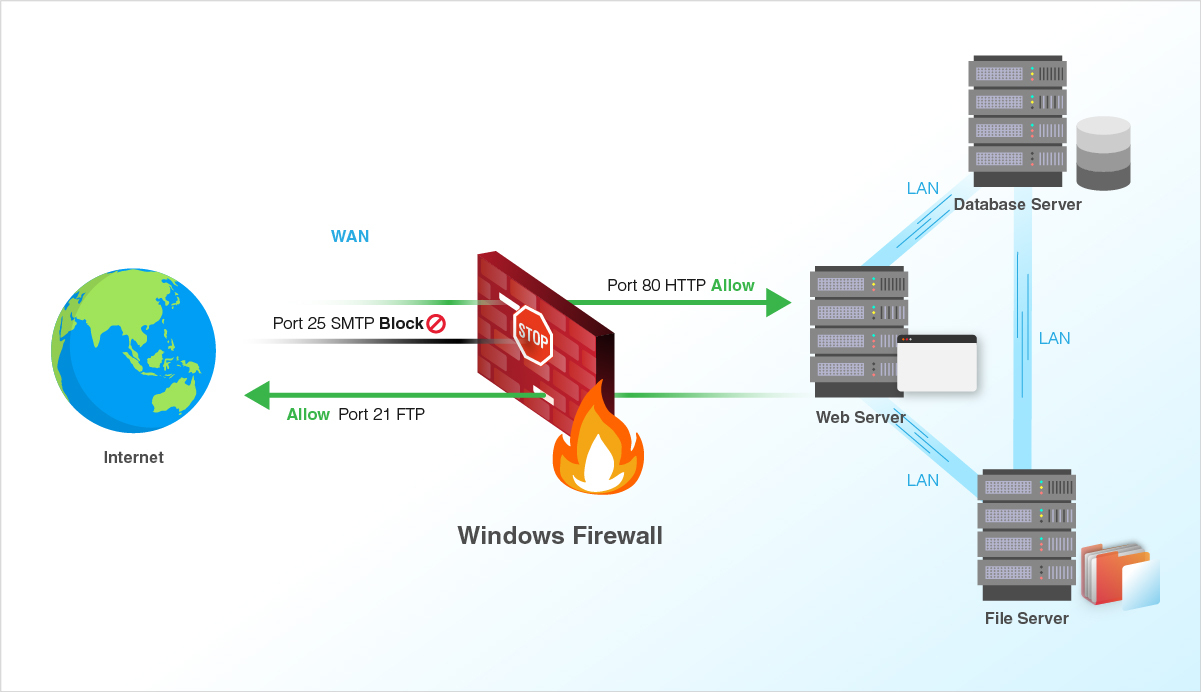
LayerStack Tutorials - LayerStack - Setting up Windows Firewall with Advanced Security on Windows Server 2019
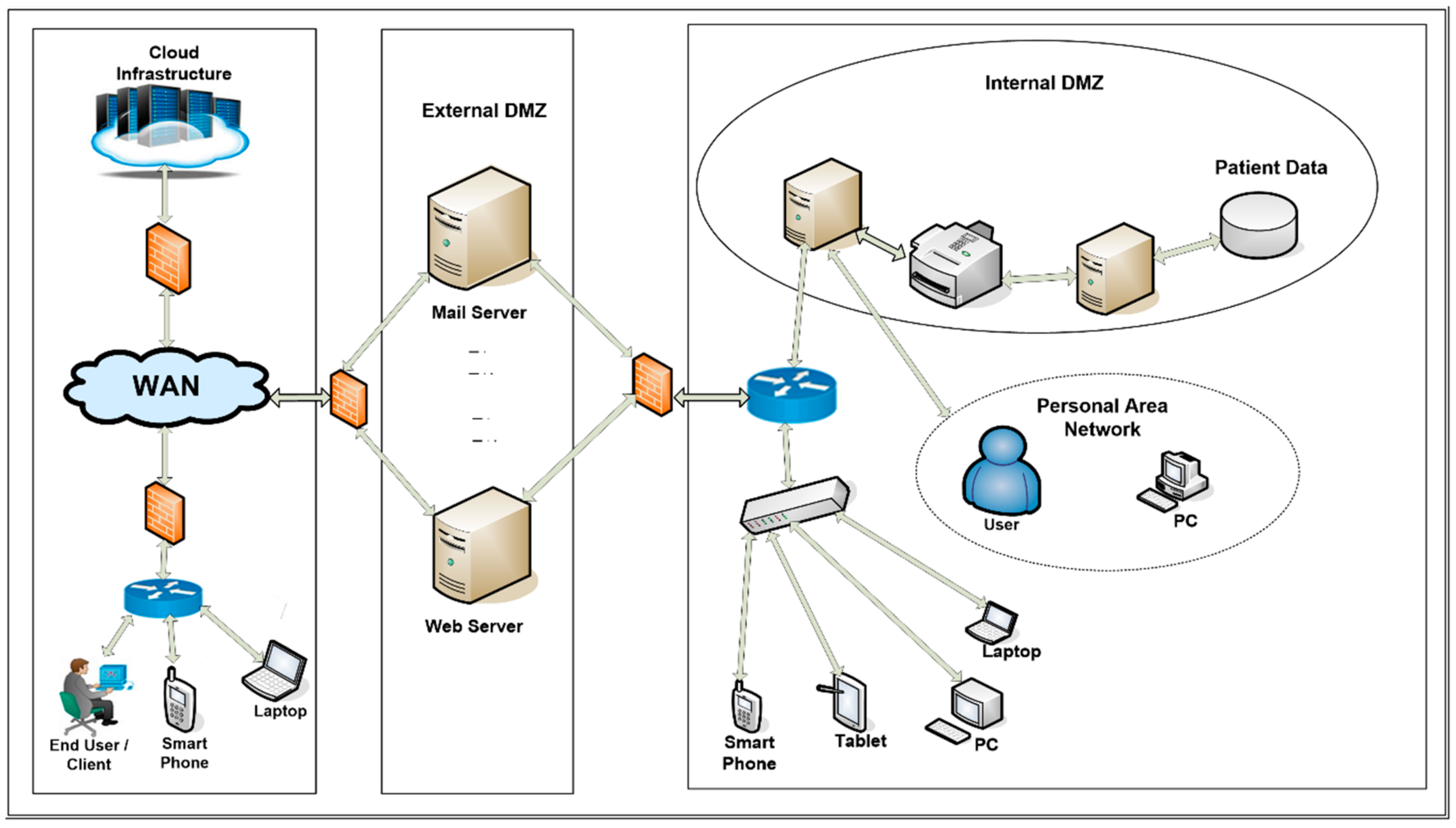
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review | HTML
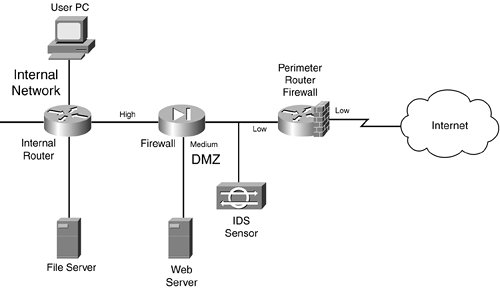
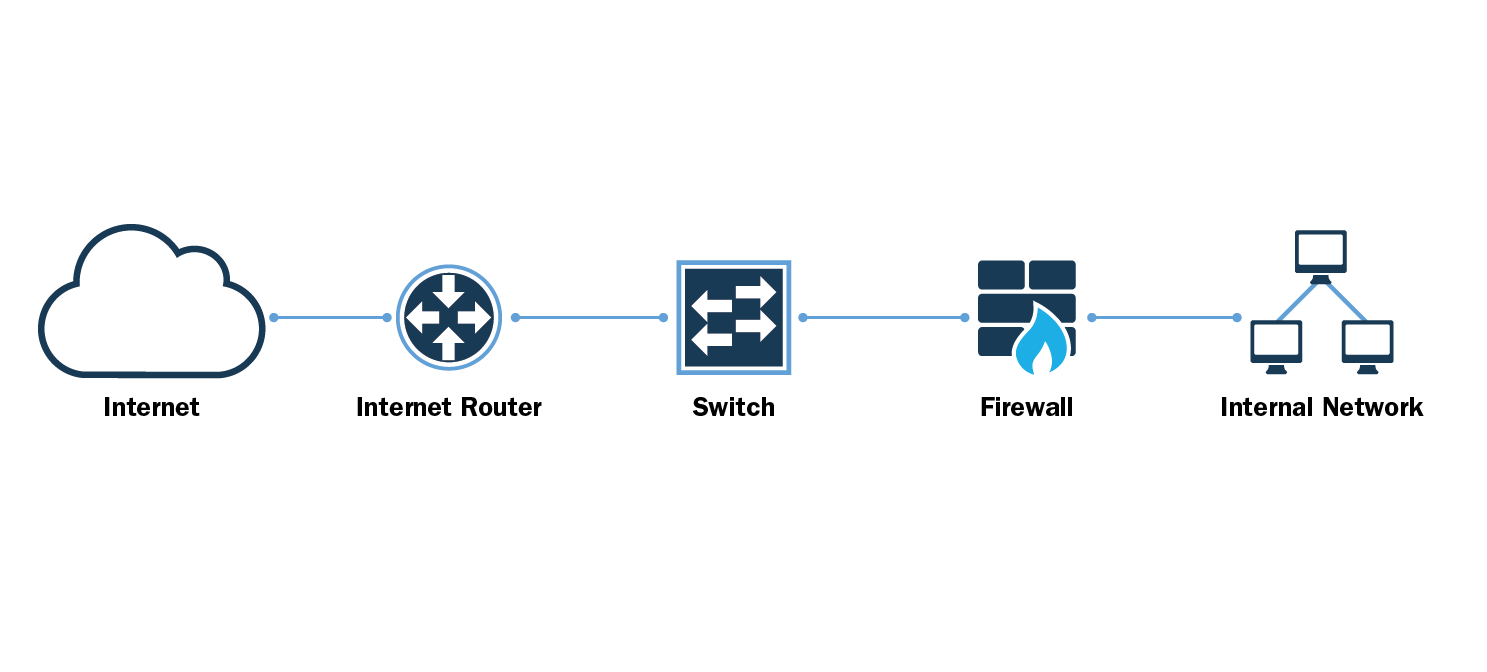
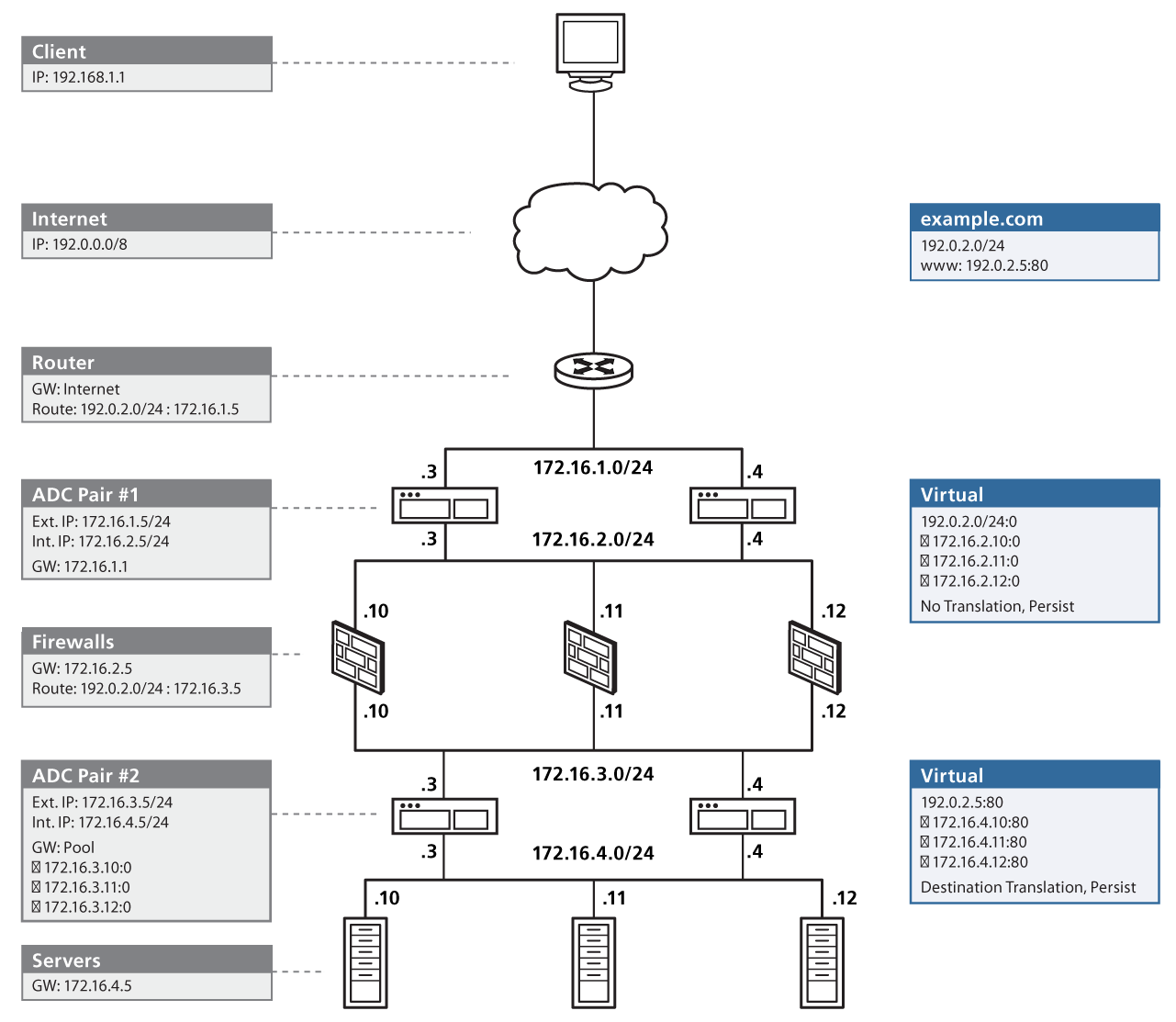
Firewall Design :: Chapter 2. Introduction to Firewalls :: Part I: Security Overview and Firewalls :: Router firewall security :: Networking :: eTutorials.org